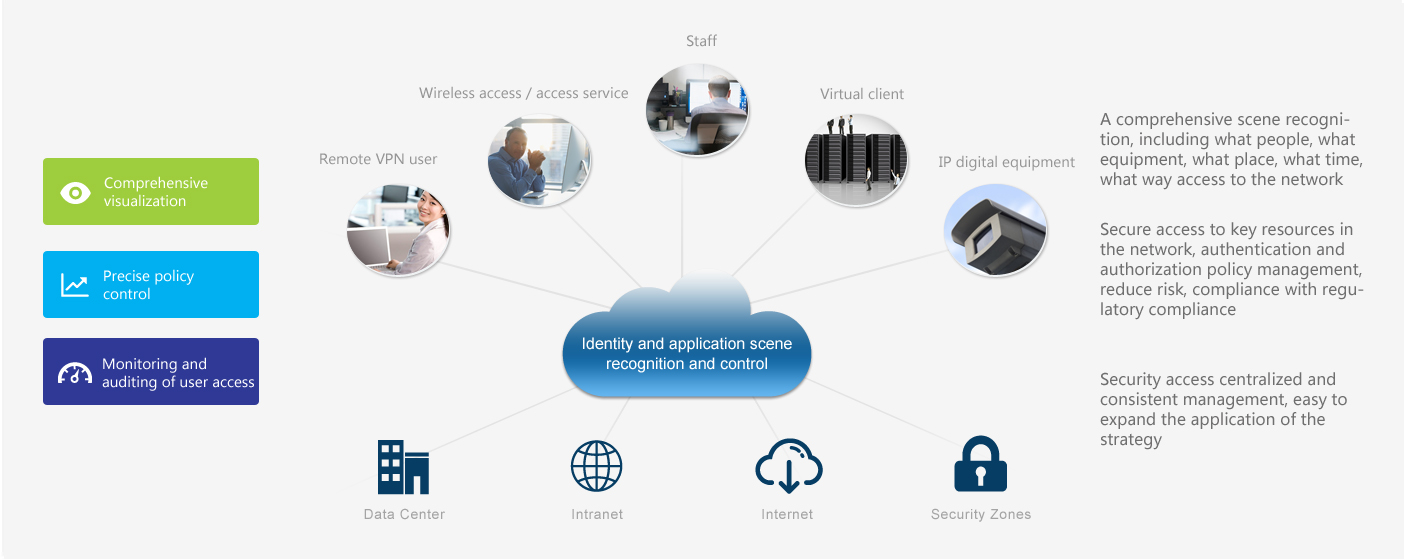
Present situation of enterprise information security
With the development of the mobile Internet, the explosive growth of mobile terminals, and rapid popularization of wireless terminals and wireless applications, development of wireless networks has been greatlt promoted.. In this era of mobile internet, wireless device has become the dominant power of the terminal access. BYOD and mobile office has become the trend of the times, and the application needs of enterprise WLAN is being further increased.With the increase of intelligent mobile terminals and popularity of enterprise BYOD, high-quality WLAN has become a rigid demand for enterprise mobile office work. And in specific application enterprise WLAN contains the following specific requirements:
Actual effects to achieve by BYOD
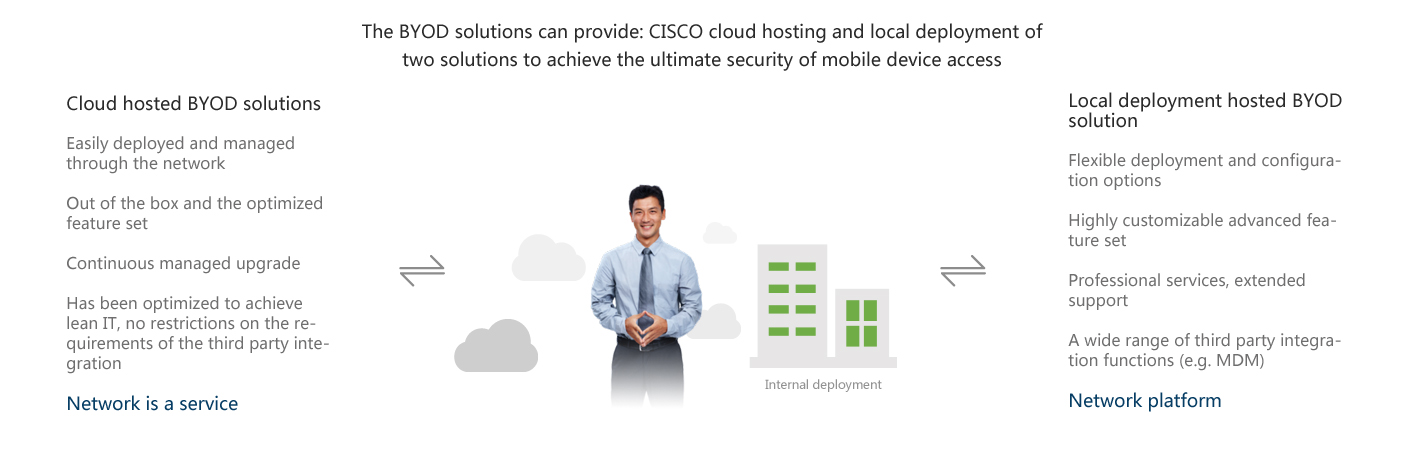
BYOD deployment scenarios and Solutions
|
|
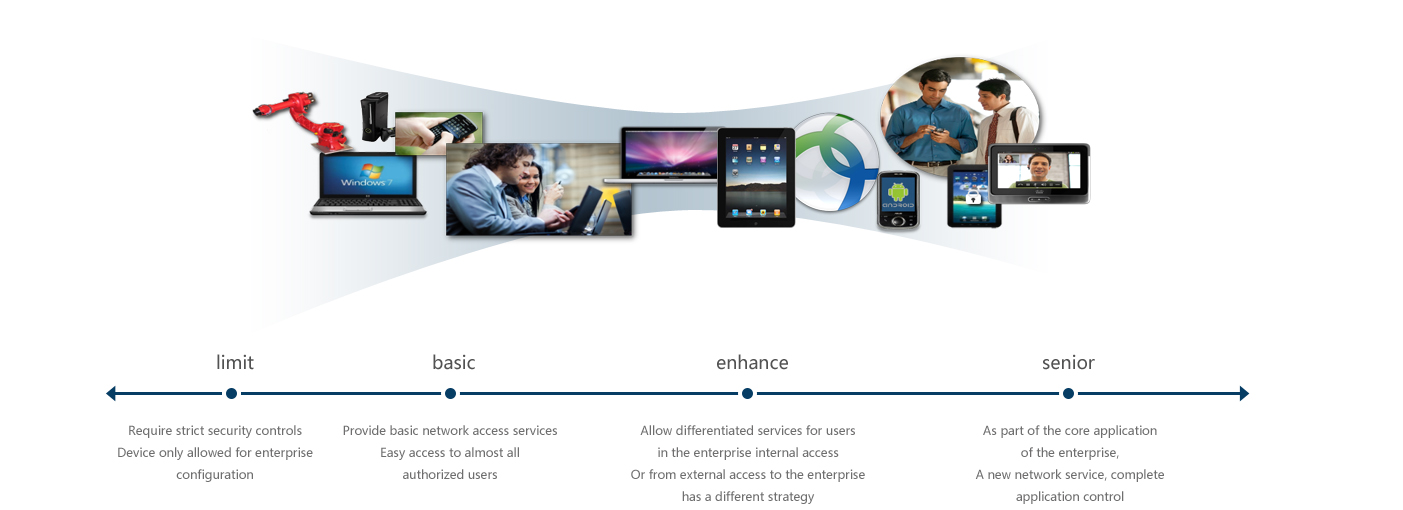
limited | basic | enhanced | senior |
|---|---|---|---|---|
| Enterprise policy | Strict control of environmental requirements | Pay attention to basic services and easy access | On-site / remote secure access to enterprise applications | All key applications, new services, full control |
| Equipment type | Equipment used by companies only | Equipment is more extensive, but is only limited to the internet simple visitors | A variety of device types + access method BYOD early business users | Arbitrary equipment, arbitrary ownership innovation organization |
| Manufacturing industry (sample) | Enterprise Limites staff’s wireless access to enterprise devices (laptops, iPad) | Enterprises to provide visitors with visiting access | Employees can use personal devices to access certain enterprise applications in the plant area | Enterprise managers use a new type of collaboration services to obtain a complete access to the application |
| IT requirement | Visibility of personnel / equipment on the network; only the company's distribution equipment can be accessed | Personal devices are limited to public Internet Limited access to internal sites is limited | Allow personal devices and corporate devices to do grain access to the network / application in the scene and in different places. | Ensure complete mobile and collaborative experience |
| To adopt solution | Core infrastructure- Wireless&wired Strategic management infrastructure-ISE | Core infrastructure- Wireless&wired Strategic management infrastructure-ISE | Core infrastructure- Wireless&wired Strategic management infrastructure-ISE Safe movement-Anyconnect | Core infrastructure- Wireless&wired Strategic management infrastructure-ISE Safe movement-Anyconnect Working space management-MDM Collaborative application-Jabber/Webex/VDI |
BYOD deployed phase program, flexible choice being made according to the actual situation of enterprises
Advantages of NORGIN BYOD Solution
NORGIN BYOD Solution includes the two respevts of BYOD management and BYOD security; from the two perspectives of management and security,, while mobile terminal management is paid attention to, it is ensured that the mobile application services deal with all links of security protection. In ensuring the effectiveness and intuitive management of the enterprise’s mobile applications, safety of BYOD is also ensured. Equal emphasis laid upon management and security is the most comprehensive and effective security solution.




 +86-21-5169 9669
+86-21-5169 9669
 +86-21-5169 9665
+86-21-5169 9665


