Cisco Secure ubiquitous threat prevention solutions
Converged networks, face more security challenges
In the traditional "defense in depth" architecture, under normal circumstances, organizations have to from different suppliers buy multiple security solution, such as firewall, VPN gateway, and web filters and other equipment. Since these products are not always well compatible, so the method will increase the complexity of. Due to the lack of uniform protection, will cause a number of blind spots. An attacker would use these vulnerabilities to attack the organization, and the organization usually has no knowledge of threats and attacks.
-

Change of network model
Evolving from the traditional local network -BYOD: access to mobile terminals; cloud environment: cloud transfer, center cloud; with increased interconnection, more locations are faced with security threats.
-

Ubiquitous threat
Zero Day attack, APT- advanced persistency attack
-

Complex / fragmented network environment and secure solutions
Complex heterogeneous environments - more vendors; more protocols; more fragmentation schemes (industrial networks, data center networks, campus networks)
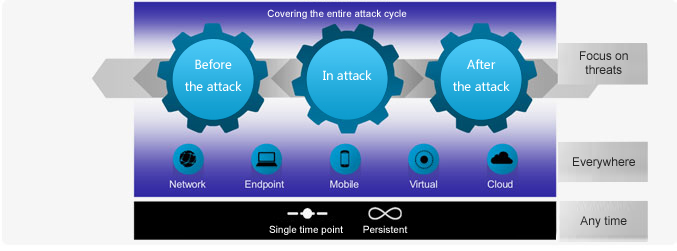
Network model of dynamic defense systemNetwork model of dynamic defense systemFocus on threatsDiscovery and reinforcementDetection, blocking, defenseLocation, mitigation / repairSafety protection is everywhere and at all times.
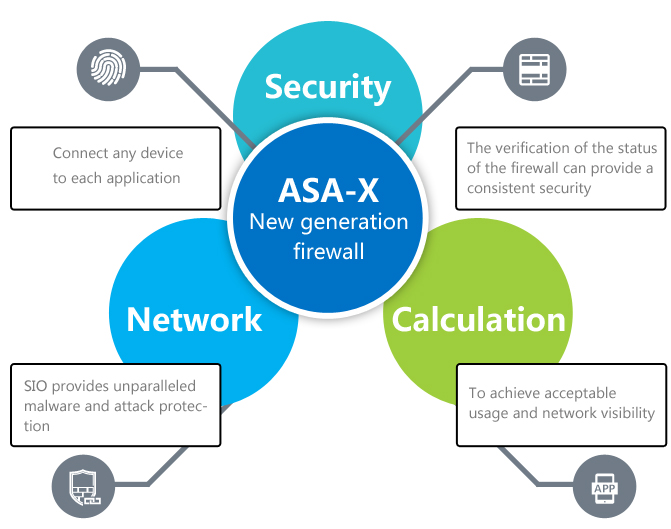
Norgin-offered threat prevention solution has such a advantage:comprehensive threat defense — A comprehensive defense of various threats, blocking not only the threat from the network layer, but also the threat from the application layer, especially HTTP slow attack for application layer and APT attack;Intelligent application analysis — To do control according to application, not based on the IP and port control as in the past, both improving the data security but learning the visiting state of enterprise applications through analysis, enhancing the visibility of them;Strong application visibility — not only providing the users with a reasonable, efficient management interface, but also a complete and detailed report, and through these statement and management interface users fully grasping application control state of the whole enterprise, timely and effectively removing and blocking the security threats targeting the enterprise application;Efficient processing performance — starting from the two aspects of the physical architecture and data model, the new technology is used to speed up the recognition and processing of threats as well as the scanning of the application data.




 +86-21-5169 9669
+86-21-5169 9669
 +86-21-5169 9665
+86-21-5169 9665


